Keycloak is an open source identity and access management solution. Keycloak ensures high performance with clustering options for scalability and availability, making it a lightweight, fast, and scalable choice for secure application and service adaptation, all customizable through code and tailored password policies. It offers Single-Sign On (SSO) for authentication, user federation supporting LDAP and Active Directory, and identity brokering for easy integration with social networks and existing OpenID Connect or SAML 2.0 identity providers.
Sign In
On your first visit to the site, you will be presented with the login/signup screen.
When your instance is first created, an account is created for you with the email you chose. You can get the password for this account by going to your Elestio dashboard and clicking on the "Show Password" button.
Enter your email, name and password and click the "Sign In" button
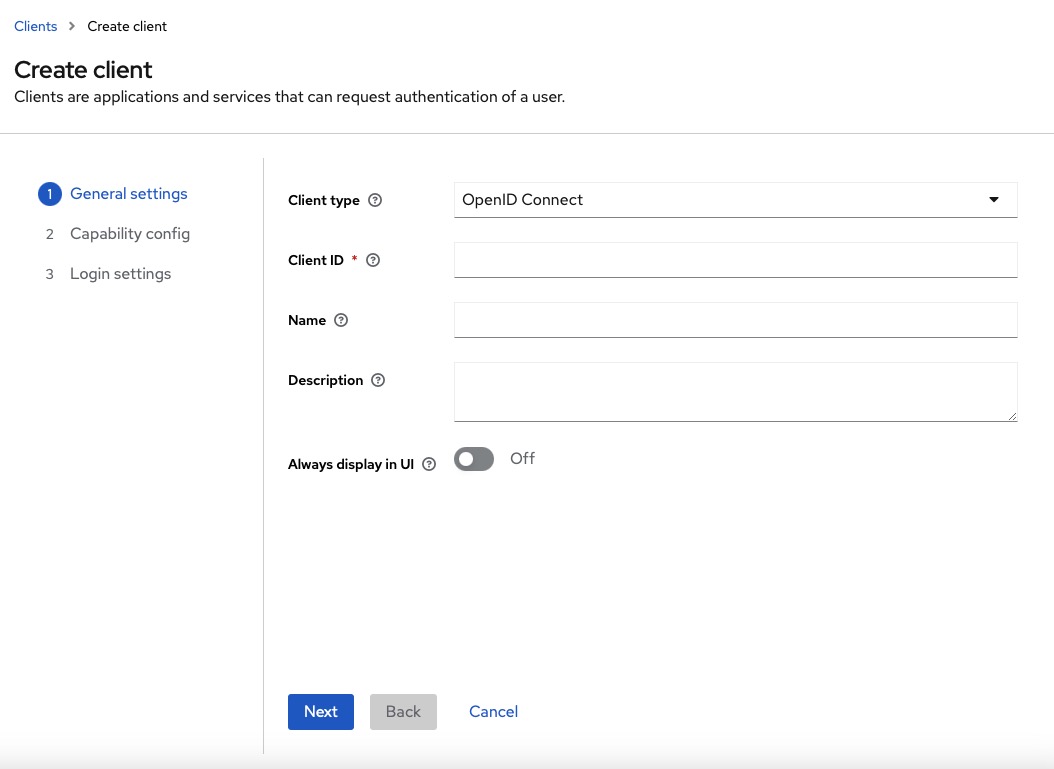
Creating Client
To get started, you will need to create a client in Keycloak. Clients are applications or services that can request Keycloak to authenticate a user. They also have the ability to request identity information or an access token to securely interact with other services on the network that are protected by Keycloak. Clients play a vital role in ensuring the security of applications and providing a seamless single sign-on experience.
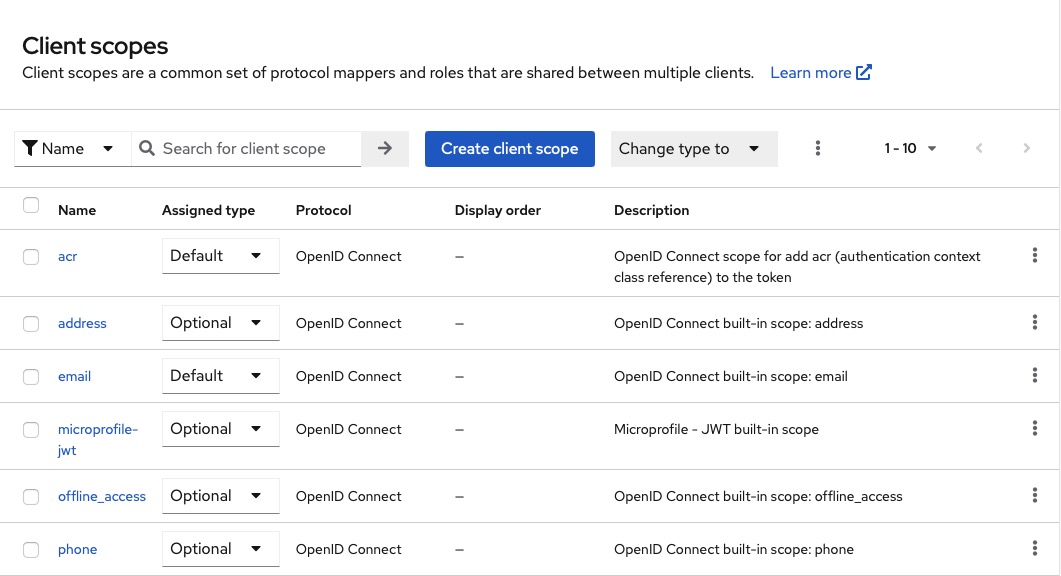
Creating Client Scopes
When a client is registered, you must define protocol mappers and role scope mappings for that client. It is often useful to store a client scope, to make creating new clients easier by sharing some common settings. This is also useful for requesting some claims or roles to be conditionally based on the value of scope parameter. Keycloak provides the concept of a client scope for this.
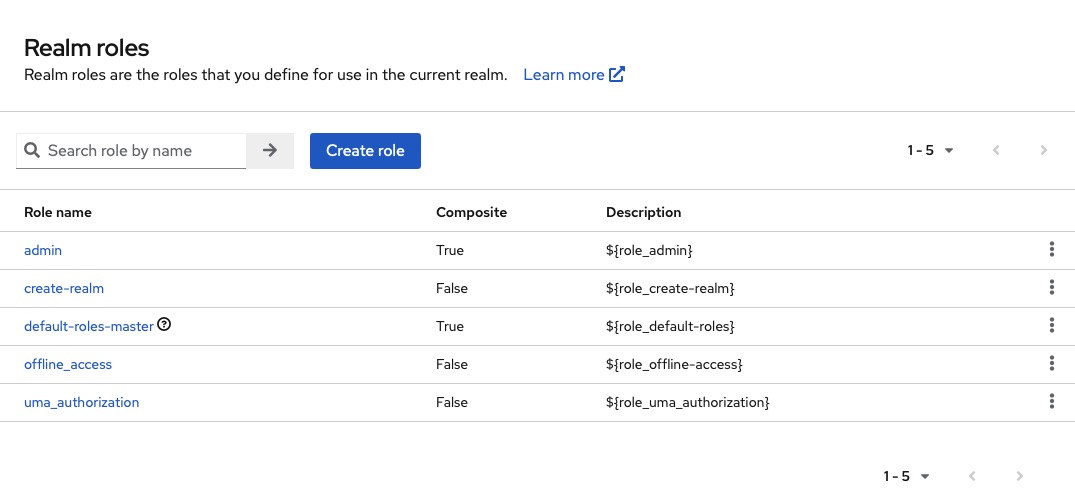
Creating Realm Roles
A realm manages a set of users, credentials, roles, and groups. A user belongs to and logs into a realm. Realms are isolated from one another and can only manage and authenticate the users that they control.
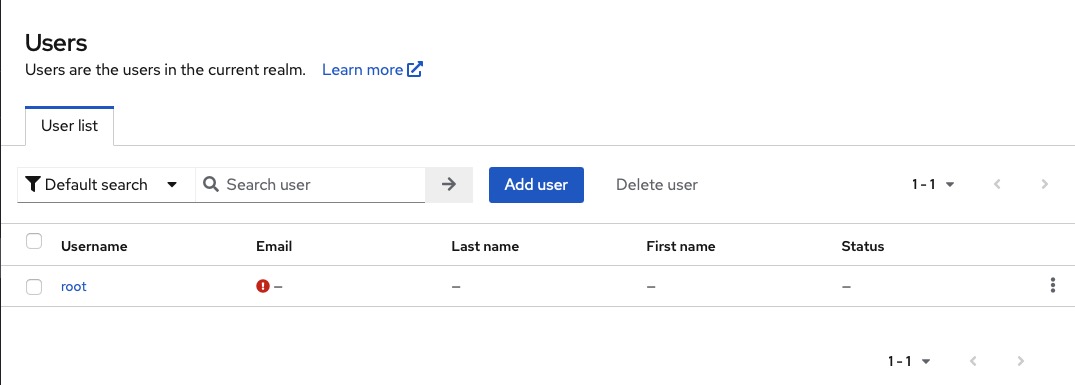
Creating Users
Users are individuals who can log into your system. They have attributes such as email, username, address, phone number. Users can be assigned to groups and given specific roles. Add new users to your Keycloak instance by clicking on the "Users" on left side.
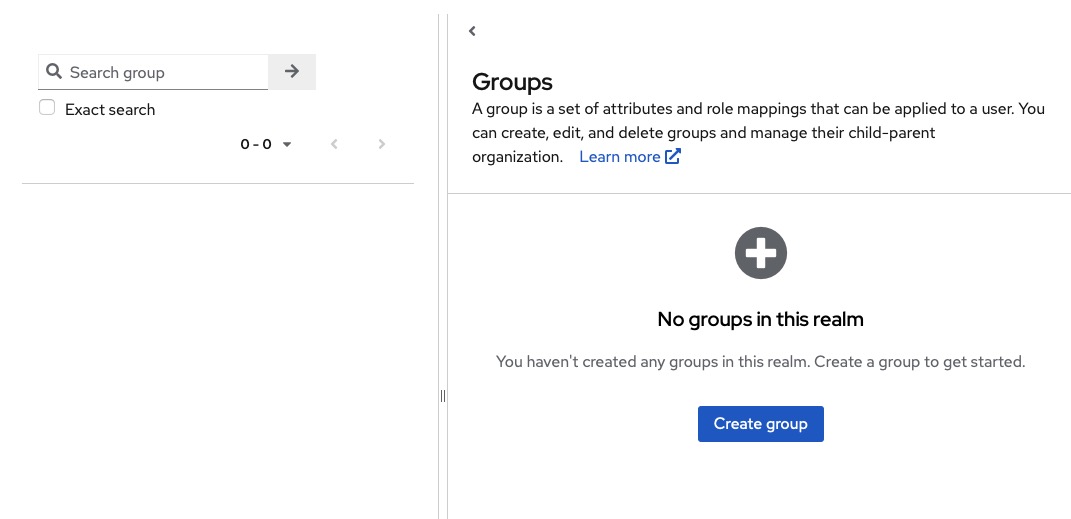
Creating Groups
Groups in Keycloak are used to manage collections of users. Groups can have defined attributes and roles mapped to them. When a user becomes a member of a group, they inherit the attributes and role mappings associated with that group. You can create new groups by heading over to the "Groups" section in the left side menu.
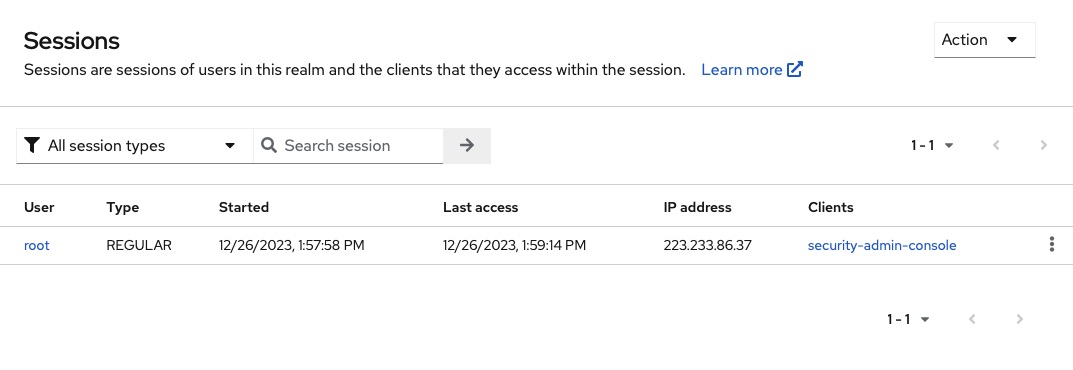
Sessions
Keycloak keeps track of user sessions when they log into realms. Within each session, Keycloak remembers the clients that the user has visited. Realm administrators have the ability to perform various actions on user sessions, such as viewing login statistics, monitoring active users and their login locations, logging out users, revoking tokens, and configuring token and session timeouts. You get to checkout the sessions by clicking on the "Sessions" on left side.
Events
Keycloak allows you to track and monitor all user and admin related events. These events include successful logins, incorrect password attempts, and user account updates. By default, Keycloak does not store or display events in the Admin Console, except for error events which are logged in the Admin Console and server's log file.
Realm Settings
Realm settings in Keycloak allow you to control various options for users, applications, roles, and groups within a specific realm. By configuring realms through the Admin Console, you can manage objects such as users, applications, roles, and groups. Each user belongs to and logs into a realm, and a Keycloak deployment can support multiple realms stored in the database.
Authentication
Authentication settings include flows and policies. An authentication flow is a container of authentications, screens, and actions, used during log in, registration, and other Keycloak workflows. Keycloak provides several built-in flows that cannot be modified, but their requirements can be adjusted to meet specific needs. Additionally, Keycloak offers password policies that can be configured through the Admin Console to enforce security measures for passwords.
Identity Providers
Keycloak serves as an identity provider (IDP), which means it can authenticate users. Get list of all the identity providers by clicking on the "Identity Providers" on left side menu. Each provider provides a way to authenticate users. Keycloak comes with a variety of built-in identity providers, but you can also add custom providers.
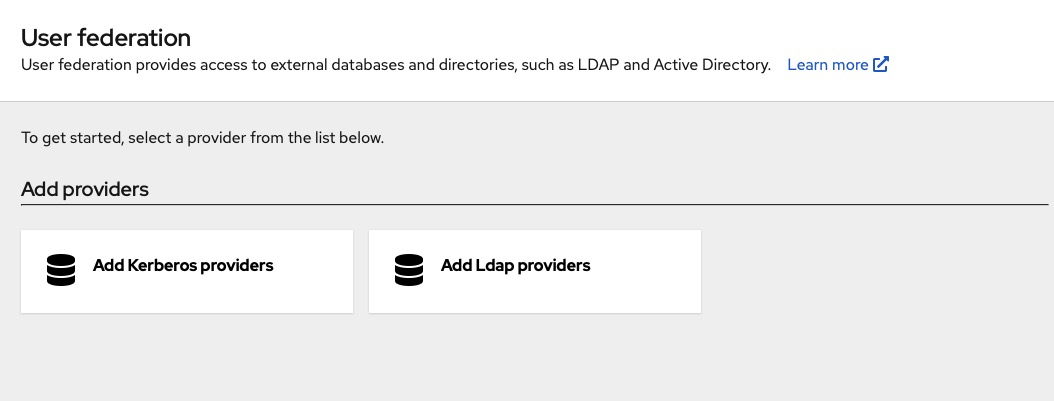
User Federation
Keycloak has the capability to store and manage user information. In many cases, organizations already have LDAP or Active Directory services that store user credentials. Keycloak can be configured to validate credentials from these external sources and retrieve identity information. You can click on the "User Federation" on left side menu to add your preferred provider.